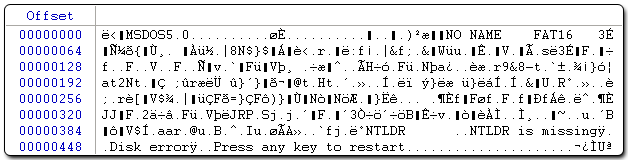
When using regular hard disks, all files that are created or downloaded are available to anyone with access to your system. Even when deleted, the data can still be retrieved with various methods including reading the data on the hard disks directly. As you can see from Figure 1, a lot of information can be exposed on a regular hard disk.
Figure 1 - Unprotected
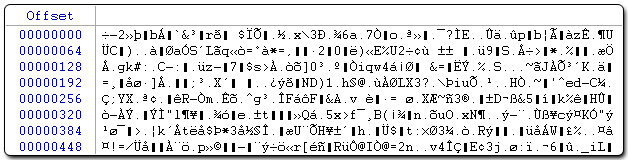
Hard Disk Data By using StealthDisk, you can help protect yourself from others spying on your important file and documents. StealthDisk volumes present themselves as regular hard disks to the user. Use them like a regular hard disk to create and store any files or documents you want. As you read or write data to the StealthDisk volume, all information is encrypted or decrypted on-the-fly as you work. The protection is transparent allowing you to work like you did without StealthDisk. The difference is the security StealthDisk provides. Figure 2 shows what the data in Figure 1 would look like encrypted with StealthDisk. Figure 2 - Hard Disk Data with StealthDisk Protection
StealthDisk also has the ability to create an External Header Block or EHB file. What this does is store all the encrypted key information associated with the StealthDisk volume in a separate file. Place this file on a USB drive or floppy disk to increase the security of your StealthDisk volumes. Without the EHB file, there is no way to mount your StealthDisk volume.
StealthDisk utilizes a kernel-based driver to provide a transparent, on-the-fly, encrypted virtual disk for the best performance possible. Using only high quality, industry-standard methods and algorithms, StealthDisk securely encrypts and protects your files and documents from unwanted access. The following are some of the techniques that StealthDisk employs. Mersenne Twister (Pseudo-Random Number Generator) The Mersenne twister is a pseudorandom number generator that was developed in 1997 by Makoto Matsumoto and Takuji Nishimura. It provides for fast generation of very high quality random numbers - having been designed specifically to rectify many of the flaws found in older algorithms. More Information on Mersenne Twister PBKDF2 (Password-Based Key Derivation Function) PBKDF2 applies a pseudorandom function to derive keys. The length of the derived key is essentially unbounded. This scheme is described in PKCS#5 which is the Password-Based Cryptography Standard. The pseudorandom function used for PBKDF2 is HMAC-SHA1.
More Information on PBKDF2 AES (Advanced Encryption Standard) AES, also known as Rijndael, is a block cipher adopted as an encryption standard by the US government. It was adopted by the National Institute of Standards and Technology (NIST) as US FIPS PUB 197 in November 2001 after a 5-year standardization process. Blowfish Blowfish is a symmetric key, secret key, block cipher designed in 1993 by Bruce Schneier and is included in a large number of cipher-suites and encryption products. Blowfish is not subject to any patents and is therefore freely available for anyone to use. This has contributed to its popularity in cryptographic software.
|
||||||